
Bugtreat Technologies Wishes Everyone a Happy New Year 2025!
Dec 31, 2024
As the clock ticks towards the end of 2024, Bugtreat Technologies would like to take a moment to reflect on the incredible..
Read more
Build a Fully Featured Online Grocery Shopping System with Grocarto
Dec 30, 2024
Online shopping has become a norm for many. The grocery sector is no exception, with more and more consumers preferring the convenience..
Read more
Create Your Own Restaurant Business App Today from Scratch
Dec 28, 2024
Explore the Foodzat App Script from Bugtreat Technologies Having a restaurant business app can significantly enhance your customer experience, improve..
Read more
Make Food and Grocery ordering and delivery from Bugtreat’s App
Dec 18, 2024
Start Revolutionizing your Online Food and Grocery Delivery with Bugtreat Technologies App Scripts. Nowadays, whether it’s ordering food from your favorite restaurant..
Read more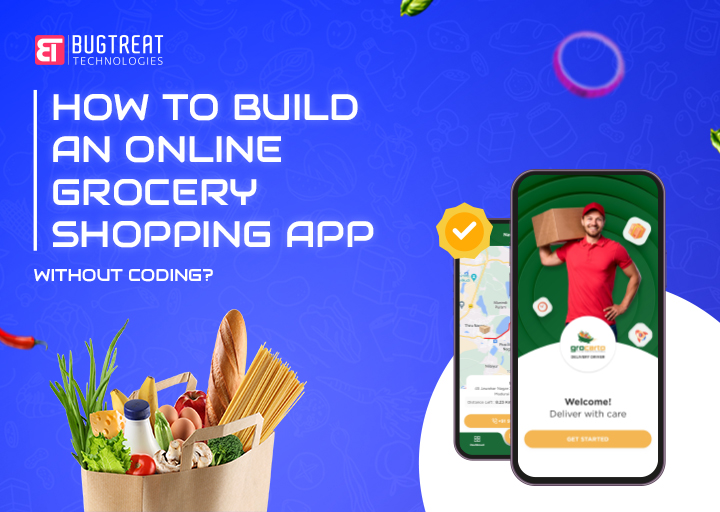
How to Build an Online Grocery Shopping App without Coding
Dec 12, 2024
Online grocery shopping apps have become increasingly popular, offering customers convenience and a seamless way to shop from the comfort of their..
Read more
Create an Online Restaurant Food Ordering System with Foodzat
Dec 12, 2024
In this fast-paced world, convenience is key, and online food ordering systems have revolutionized how people enjoy their meals. Whether it's lunch..
Read more
Think of starting an Online Food Zone? Build with Food
Nov 27, 2024
In this digital world, where convenience meets taste, starting an online food business is not just trendy—it’s essential for reaching a broader..
Read more
How to select the best Online Food Ordering and Delivery
Nov 22, 2024
In today’s fast-paced world, the demand for food delivery services has skyrocketed. With the growth of online food ordering platforms like UberEats, DoorDash, and..
Read more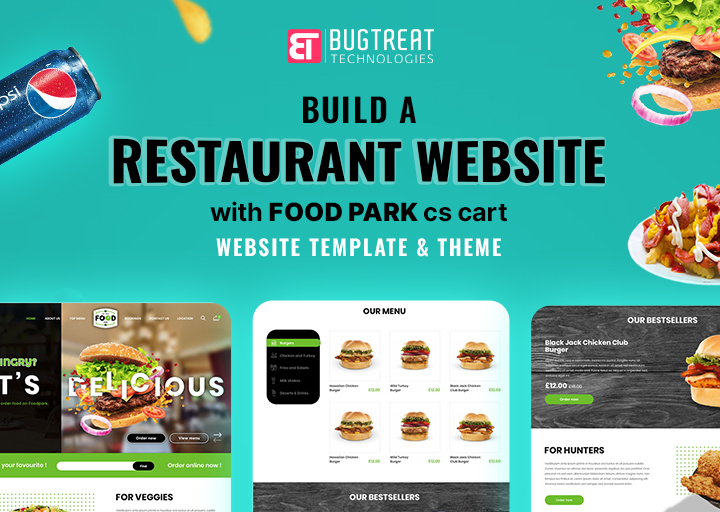
Build a Stunning Restaurant Website with Food Park CS-Cart Theme
Nov 14, 2024
In the digital age, a professional website is essential for any restaurant seeking to attract new patrons and retain loyal ones. With..
Read more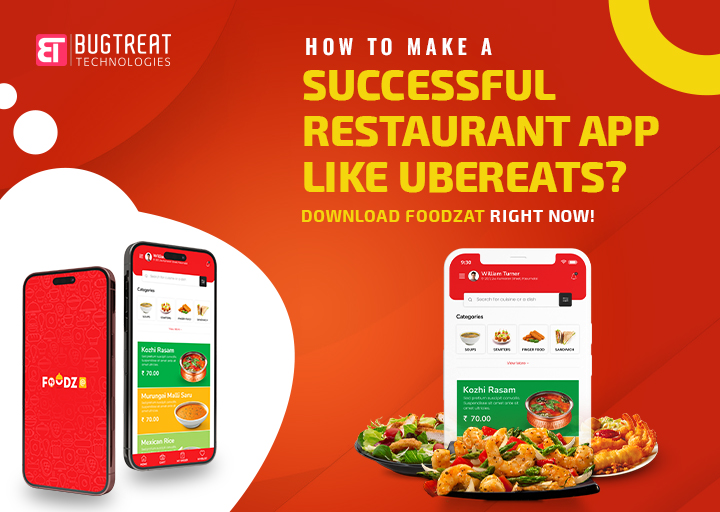
How to make a successful Restaurant App like UberEats? Download
Nov 12, 2024
Let's see the brief key steps and insights on how to make a successful restaurant app! The digital age has..
Read moreOur Latest Blogging

Google’s Very Next Algorithm: Mobile Friendliness Ranking
Mar 06, 2015
After a long gap, Google will be going to launch one another new algorithm i.e. Mobile-Friendliness Ranking Signal from April 21st 2015. Hope this algorithm..
Read more
How TO Upload A Video To Youtube
Feb 24, 2015
Hi all now we are going to see how to upload a video to YouTube for this you should have an YouTube account you can..
Read more
How To Block Multiple IP Addresses Using
Feb 20, 2015
Sometimes we need to ban particular visitors to access our website. For this, the most common reason is spammers and scrapers that perform malicious activity..
Read more
Some Useful Mac OS X Terminal Commands
Feb 19, 2015
Here are some useful Mac OS X Terminal commands that bring you more change and comfort in your working with Mac. 1. Customize OS X..
Read more
Force quit OS X menu bar apps
Feb 19, 2015
To force quit a Mac app, you can call up the Force Quit Applications menu from the Apple menu button in the upper-left corner or..
Read more
How To Setup Cron Job In Windows
Feb 19, 2015
You have to follow below some very simple steps to run cron file in windows system. 1. The First thing you should do is to..
Read more
Facebook launches Call-to-Action button for Business Pages
Feb 19, 2015
Want to increase leads towards your business? The big social network “Facebook” introduces call to action button to the business pages that you’re creating redirect..
Read more
Windows 10 Free upgrade
Jan 22, 2015
Microsoft windows 10 will offer a free upgrade for the users windows 8.1 first and then also for the users windows 7 by next and..
Read more
Bugtreat Technologies Wishes Happy New Year 2015
Dec 31, 2014
We think it’s the right time to share our happiness with all of our customers. Though Bugtreat had faced lot of challenges last year, by..
Read more
Mega Festival Bonanza Offer on Cs-cart Templates
Dec 20, 2014
On this auspicious festival occasion, we would like to share a glad news that we announce a drop in cost of our core website templates..
Read more
